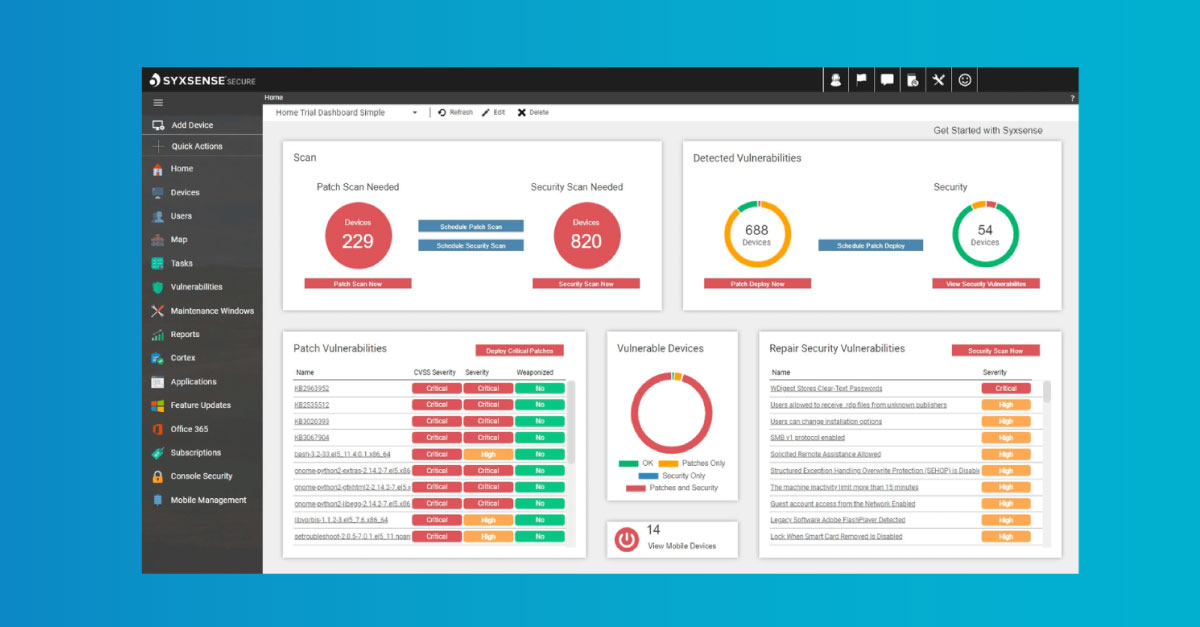
Be more cyber secure with VLCM Cybersecurity
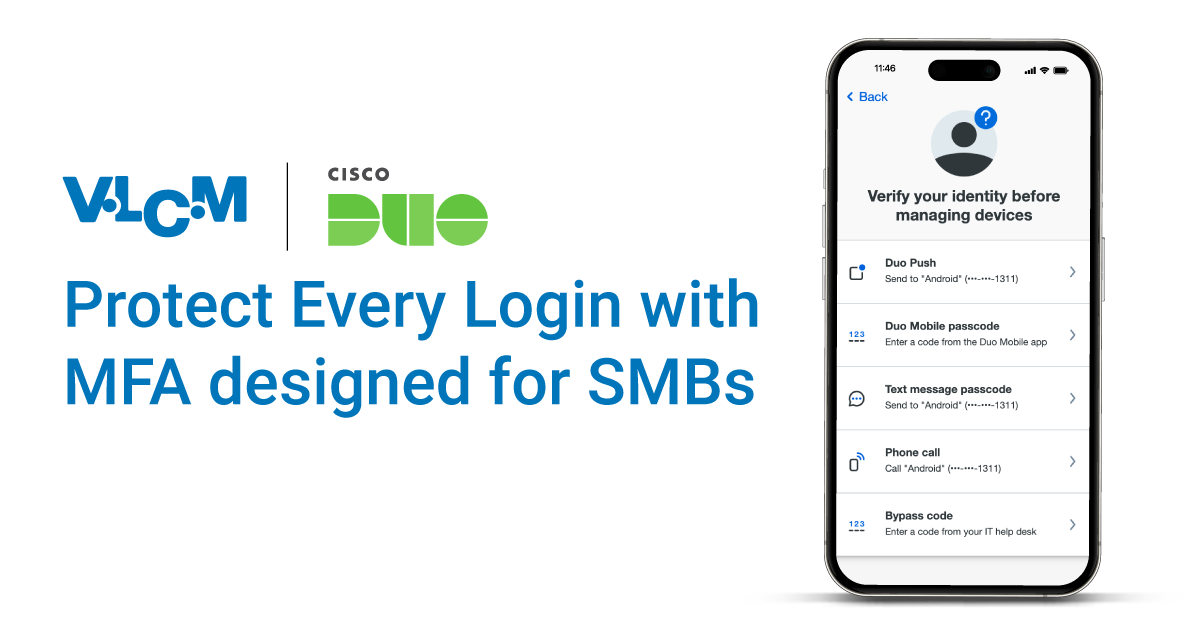
Protect your business from relentless cyber threats with VLCM's comprehensive cybersecurity services. Our expert team delivers advanced solutions and strategic insights to secure every aspect of your organization. With VLCM, you can have peace of mind knowing your business is fortified against potential threats and compliant with industry standards.















.jpg)