
Securing your data everywhere. Data at rest, in motion, at execution.

Today enterprises are struggling with more advanced and persistent threats such as ransomware and malware that targets the low levels of the IT infrastructure, beyond the reaches of their end point security software solutions.
With cyber attackers increasing their aggressiveness, their scale and budgets, they are creating an increasingly sophisticated marketplace for new exploits to occur.
To address the security challenges across highly distributed IT environments HPE’s approach begins at the foundation—in the supply chain and rooted in the silicon with enhanced zero trust enabled 360-degree security for Compute.
HPE’s zero trust security architecture and secure lifecycle is initiated deep in the silicon during manufacturing and concludes with a safeguarded, end-of-life decommissioning, to create the world’s most secure industry-standard server portfolio. Right now around the world, you can find the HPE-exclusive silicon root of trust technology in over two million active servers.
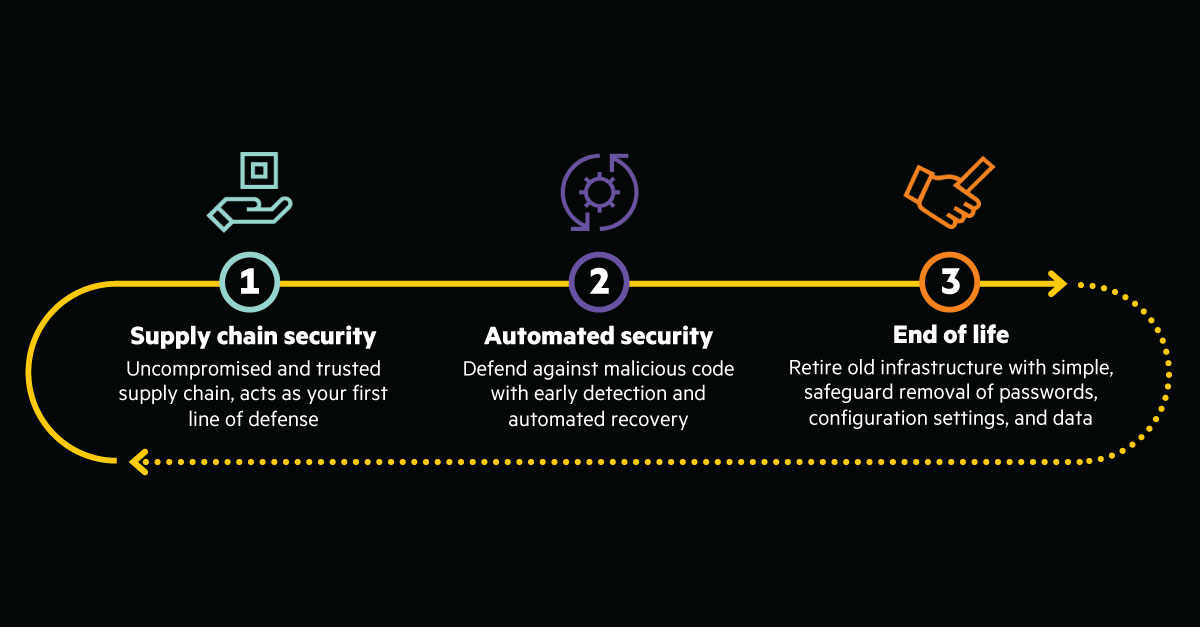
Extends the Silicon root of trust further across the ProLiant architecture with Platform Certificates to enable zero-trust provisioning.
This document provides an overview of HPE approach to Zero Trust Security for all BUs. Zero Trust security is a philosophical approach to protecting data, and focuses on identity and access management.
Get 360-degree security where and when you need it.
Submit the form or contact a VLCM representative today.